Cybersecurity
Spirent offers advanced security testing platforms, seasoned security specialists with industry-specific expertise, and realistic application load and threat traffic emulation.

Spirent CyberFlood
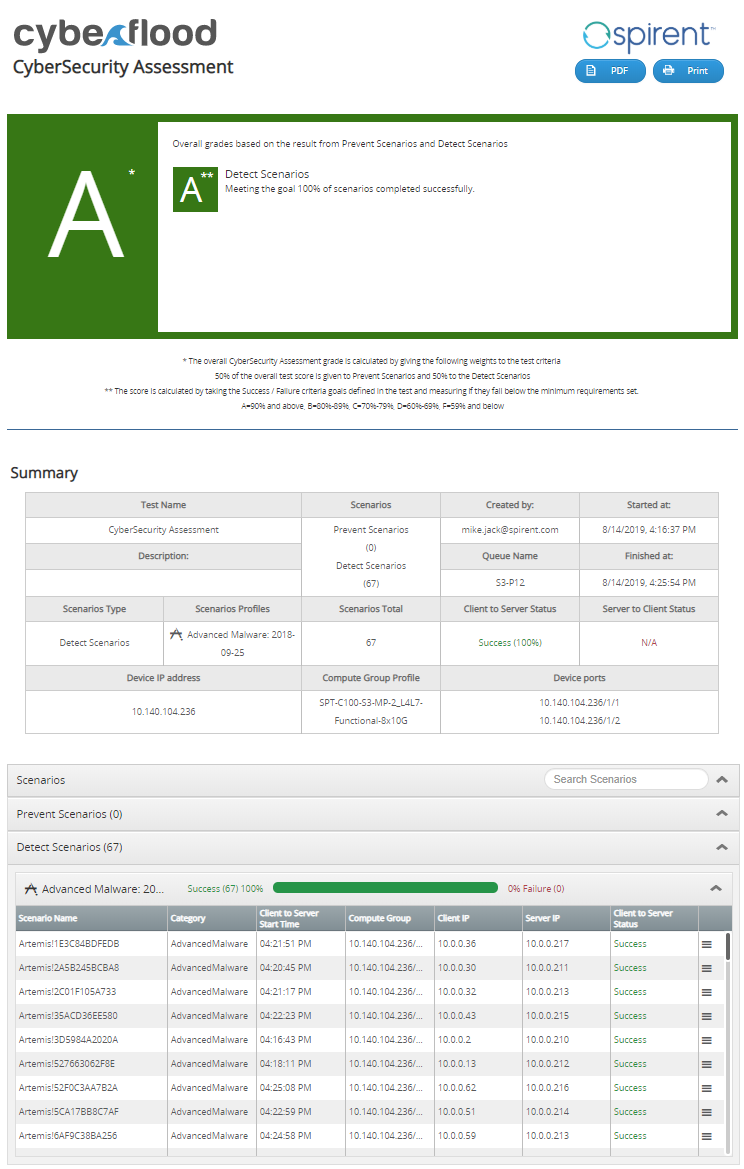
Spirent CyberFlood is a powerful, easy-to-use test and assessment solution that generates thousands of different realistic application, attack, and malware scenarios to validate the performance, scalability and security of today’s application-aware network infrastructures.
Unlike other test solutions, CyberFlood emulates real high-performance user applications and security traffic based on actual application and attack scenarios for realistic security, load and functional testing.
With CyberFlood users can quickly and easily assess security devices and counter measures with the latest applications and zero-day applications attacks/ malware (updated and downloaded to CyberFlood continuously), all with unparalleled realism and scalability. Users can push their solutions to the limit while ensuring their infrastructure will stand up to real-world demands.
Advantages of CyberFlood
- Available across Multiple Platforms
- C1 Appliance: Portable bench level 1/10G testing
- CF20 Appliance: Self-contained 1/10/40/100G testing
- C100-S3 Appliance: High-end Service Provider/Carrier grade performance for 1/10/25/40/50/100G testing
- CyberFlood Virtual: Software based application and security testing framework for virtual and cloud environments such as AWS and Azure
- Agility – comes with Spirent TestCloud giving you access to tens of thousands of applications, malware and attack scenarios
- Easy to use – web based interface makes configuring, running and managing tests quick and easy for all levels of users
- Real-world test conditions and traffic and attack mixtures including DDoS scenarios
- CyberFlood Data Breach Assessment provides continual production network security validation
- SmartMutation based fuzzing for next generation firewall aligned protocols – perform different service and protocol mutation scenarios for HTTP, HTTPS, TLS, QUIC and much more